Disclaimer: This article is the result of a few weeks of research. I did report the most disturbing things I found to the owners of the servers if I could find out who they are and the other problems were reported to Cert.at. Also I didn't try to login to any device/service/site that required a password.
First of all: How do you even get all IP addresses of a whole country?
This is very simple. IP adresses are not just "generated" by a country but rather assigned by a central authority. This means that there are lists of all IPs and their assigned countries.
Anyone can download such a list, enter grep Austria IP2LOCATION-LITE-DB1.CSV > austria.csv and run a simple script to convert the IPs to a usable format.
Austria has 11 million IPv4 addresses. 11.170.487 to be exact
If you don't want to play around with IPs yourself, you can also use Shodan.io
First thing to check: Are any unpatched Windows machines on the net?
Surely no sysadmin in Austria would expose unfiltered Windows SMB ports to the Net, would they?
masscan -p445 --rate 300 -iL austria.ips -oG austria.445.scan && cat austria.445.scan | wc -l
1273 directly exposed Windows machines found
Oh boy. This fact alone would make most sysadmins sweat but since the ETERNALBLUE exploit was published by the Shadowbrokers, most IT people would agree that having unprotected Windows machines slurping on the web would not be a good idea.
The upside: None of the 1273 machines were vulnerable to ETERNALBLUE
Enough about Windows, what about open resolvers?
Have you ever heard of open resolvers? If not you must have heard about DDoS attacks. This is a real problem for the web.
It works like this: An attacker sends a small DNS query from a spoofed IP address (the one of their target) and the server responds with a much larger package to the spoofed IP. So the attacker only uses 40 bytes and the open resolver responds with a 4000 bytes answer to the victim. This way an attacker can pin down large company servers with no more upload speed than a normal smartphone can produce. Which happens fairly often
Let's check how many open resolvers are hosted in Austria
Let's scan all of Austria for Port 53 UDP
I have found exactly 8728 publicly exposed DNS servers in Austria. 0.08 % of all Austrian IPs are hosting DNS servers. Ok but most of them are secured
masscan -pU:53 -iL austria.ips -oG austria.53.scan && cat austria.53.scan | wc -l
But that doesn't mean much. More important is: Are these DNS servers also open resolvers?
Finding open resolvers
The method is simple: I'm using the command dig to find out if one of the IPs will resolve any address I'm feeding it. I looped the whole ip file and ran each Ip against dig +short test.openresolver.com TXT @ip.of.dns.server if it responds with "open-resolver-detected" I log and count it.
Sadly.. using this method I found out that around 25% of all austrian DNS servers were open resolvers. But to put it in perspective this is only about 0.02% of all Austrian IPs
What else is exposed in Austria?
Glad you asked. The easiest thing to scan for is port 80 (Web servers and proxies)
Webservers
67.626 Austrian IPs answer on Port 80 (http). 40.776 of them answered my IP to a simple GET request (like a browser would send it) and if you remove the ones that produce error messages we get 17.392 webservers that are actually serving something.
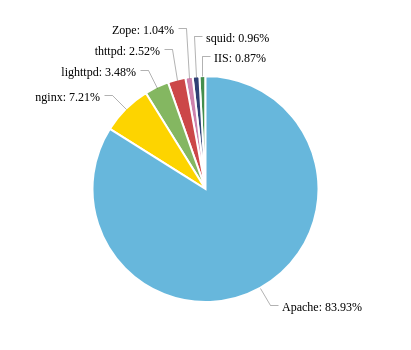
Apache is the most used web server (that sends a "Server" header). The oldest version I found was Apache 1.3.12 from 2012 running on a windows server. Double yikes.
Also I found 4 servers running on a Windows CE device. Windows CE was published in 1996 and they stopped patching it in 2013.
Visualizing 17000 Websites
I wrote a script that uses WKHTMLTOIMAGE to make a screenshot of every website and then wanted to create a collage. The first collage was pretty boring since there are many websites that only displayed white sites or error messages which I filtered by counting the number of unique pixel colors in all of the images and deleted those with just a few colors.
Just keep in mind that this is just what you would see when you would surf to the IP via a webbrowser. This doesn't mean that these are all Austrian websites, just the raw servers.
Here is the final collage of all websites I found

Printers.. because.. why not?
I found 9 HP printers without logins fully exposed to the web. There were no passwords and even printing worked.
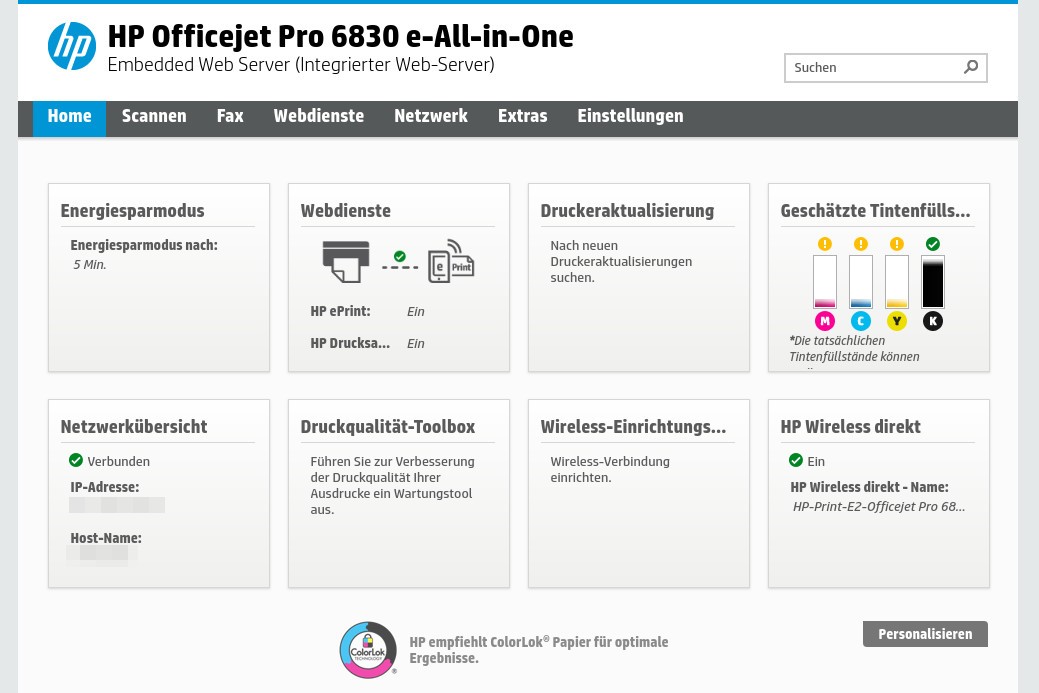
This one had also the ability to send Fax via the website. Good for the owner: The Fax number of the device was logged on the device so I found a contact and the device has since been removed from the web. Success!
Webcams
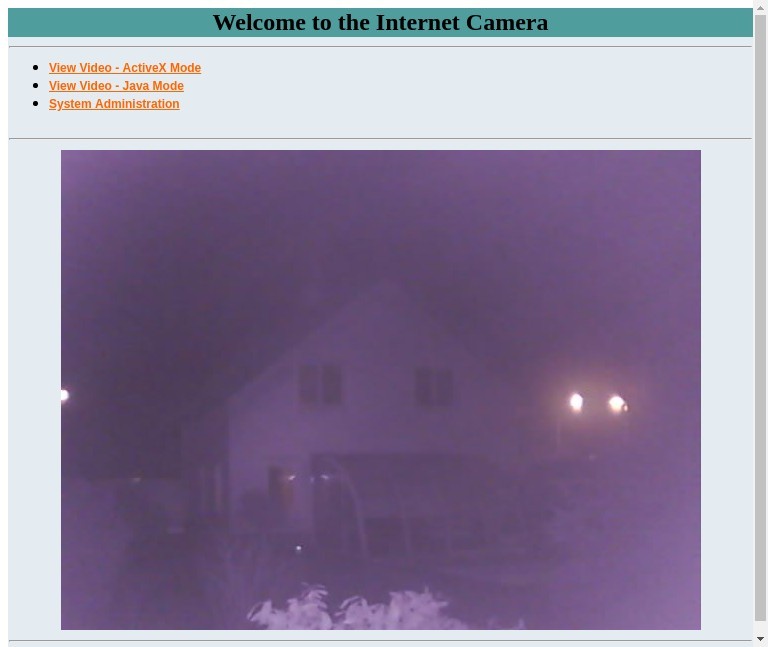
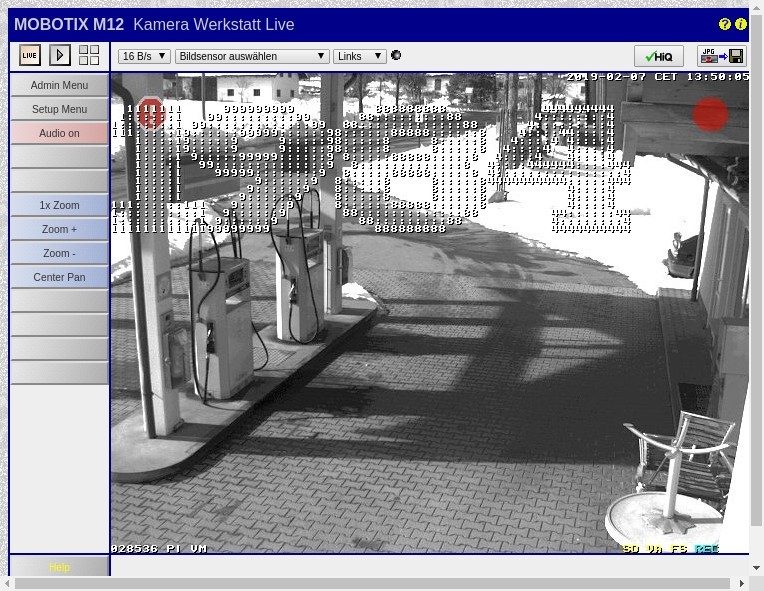
These are just 2 of over 300 IP cameras that broadcast livestreams without logins. If you want to see all of them go here: https://www.insecam.org/en/bycountry/AT/
Let's end with some of the miscellaneous things I've found
Conclusion
Austria is a small country but it has the same problems as larger countries when it comes to IT security. We need to develop a better sense for what's secure and what isn't and also providers and device manufactures should help us with safe pre-configurations.
Companies should hire good IT admins (like Haschek Solutions) to keep an eye out on what they are exposing to the web and keeping their servers patched.

Comment using SSH! Info

