Last week I got a message from my dad (who works with me at a client) with an image attached.

I asked him to unplug it, store it in a safe location, take photos of all parts and to make an image from the SD card (since I mostly work remote). I have worked on many Raspberry Pi projects and I felt confident I could find out what it does.
At this point nobody thought it was going to be malicious, more like one of our staffers was playing around with something.
The parts
There were 3 parts:
- A Raspberry Pi b first generation
- a mysterious USB dongle
- a 16GB sd card (a fast one)

First thing to do: Ask everybody who can access this network closet
The number of people who can access this small cabinet is very limited. Only 4 people have a key for this room:
- The manager
- The groundskeeper
- My co-worker
- Me
None of them knew anything about this so I asked my IT colleagues and they were as baffled as I was. I heard of people getting paid to put things like this in places they shouldn't and for this reason I was very interested in finding out what it actually does.
What is that USB dongle though?
To help me solve this mistery I asked reddit and surely enough they identified the dongle as a microprocessor, almost as powerful as the Rasberry Pi itself: the nRF52832-MDK. A very powerful wifi, bluetooth and RFID reader.

This was - no doubt - to give the old Raspberry Pi a wifi and bluetooth connection. Great so now this thing has wifi too..
Time to dissect the SD card image
The SD card has a few partitions. Most ext4 (linux) and one fat16 (boot)
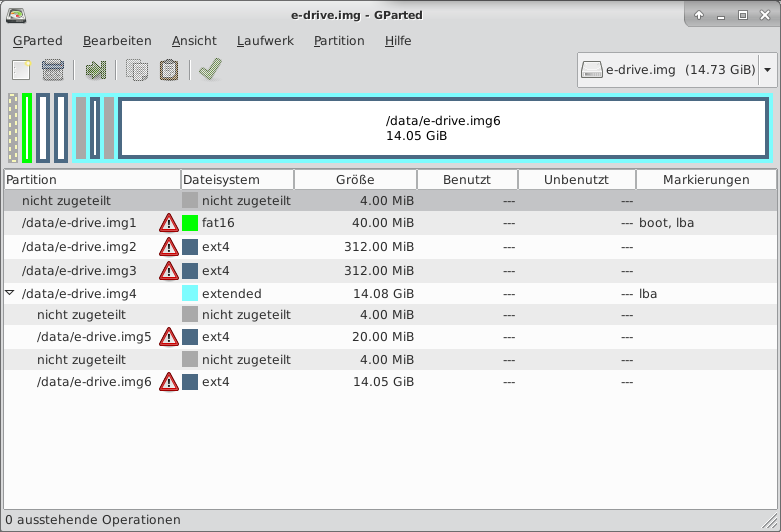
Great, time to mount it.
My debian box told me the first big clue: It's a resin installation
WTF is Resin?
Resin (now renamed to Balena) is a paid IOT web service where you can generate images for IOT devices, deploy those devices and get updates and data from and to resin.
Resin also installs a VPN on the device so the collected data is transferred securely. Obviously this device was meant to be picked up again since it leaves a trail as the service is a paid one.
Closer look at the partitions
First partition is called "resin-boot"
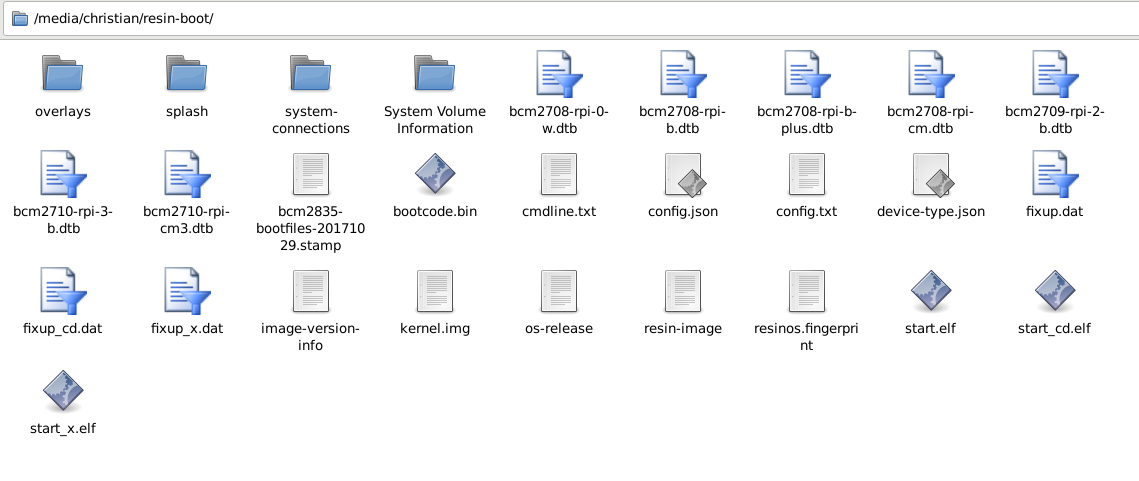
See something that catches your eye? We got a config.json. Quick jackpot?
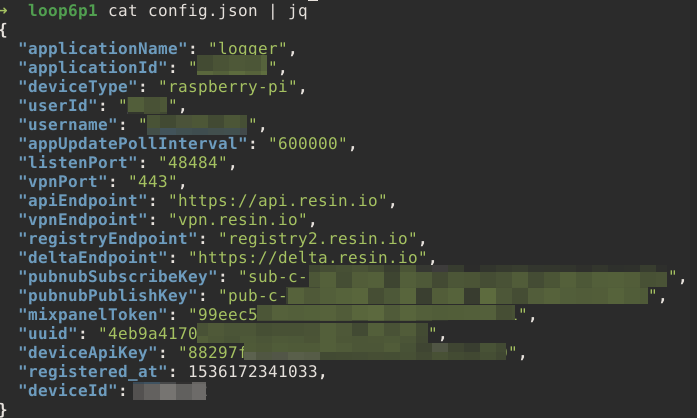
What we can extract from this file:
- The application deployed to this resin device is called "logger". Not a good sign
- We got a username. This seems to be the username for the resin account associated with this device
- Confirmation that the device used a VPN via Port 443
- A registration date. It was registered (or first deployed or set up?) on May 13th 2018
About that username..
When I googled the username found in the config.json file I found a person in the same town where this Pi was found. The company then checked their records for this person but found nothing.
Oddly enough I found a website from 2001 where parents of "gifted children" write articles about them and for some reason sign those articles with their home address and phone numbers. So I have a name and the address of this whole family.
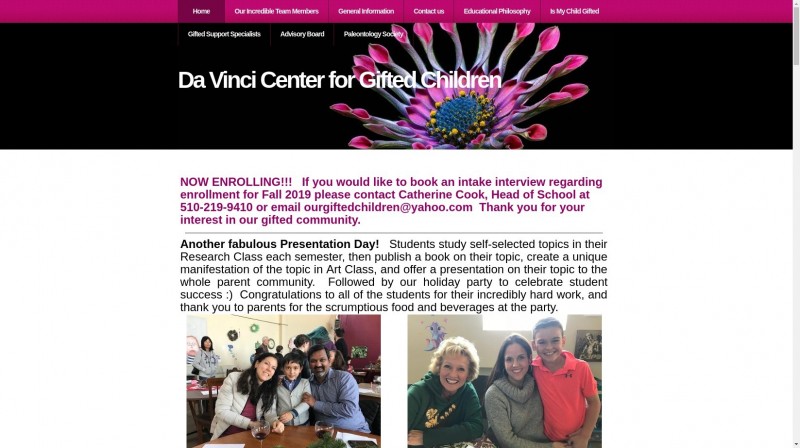
This could be a wrong lead as usernames tend to be used by multiple people but let's just keep that name in mind.
resin-data
The data directory didn't have any data stored (as in: collected data) but there was a nodejs app which was heavily obfuscated and to this day I can't tell exactly what it was doing. It seems to talk via a serial connection to the dongle but I can't extract what data is actually collected. I can only assume that it collected movement profiles of bluetooth and wifi devices in the area (around the Managers office) and maybe raw wifi packets.
But I found something much more interesting: a LICENSE.md file
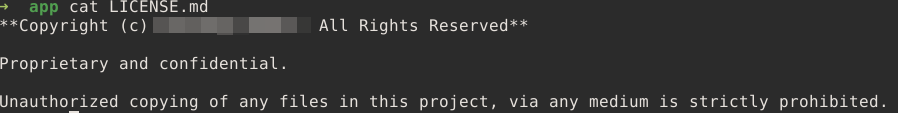
Odd.. Why would this nodejs app include a confidential piece of software? I googled the company from the copyright header and guess what?
The guy from the username I found in the config file is a part owner
It is beyond me why a co-founder of a company would distribute these devices around town but well..
Getting the attackers home address
Another very interesting thing I found was a file on the third partition (resin-state) in the path /root-overlay/etc/NetworkManager/system-connections/. The file is called resin-wifi-01 and guess what it contains?
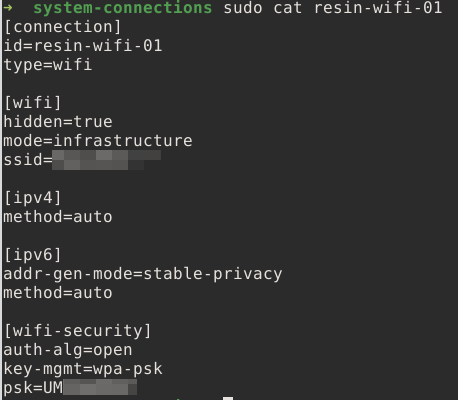
It contains the wifi credentials to the wifi that was used to set the device up (or to test it). Definitely not the wifi of the company. And what do we do, when we want to find out a location associated with a wifi name? We go to wigle.net, enter the SSID (=wifi name) and it tells us where on the world it is found.
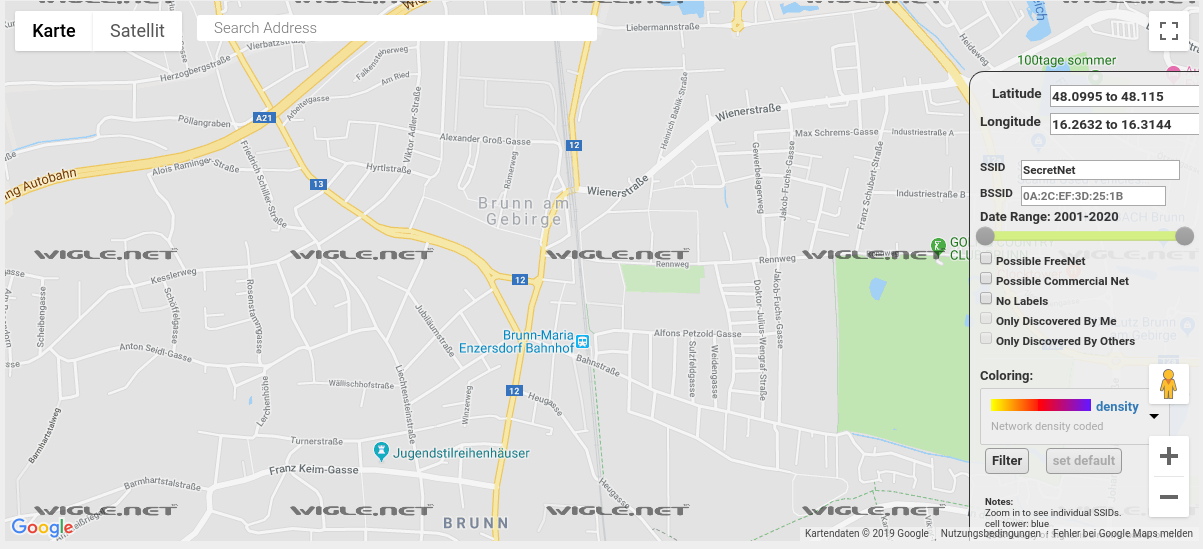
And guess what? The address we found of that gifted persons parents? That's exactly where our Pi was set up according to Wigle.net
Aftermath
How and when did the Pi even get there?
I checked the DNS logs and found the exact date and time when the Pi was first seen in the network. I checked the RADIUS logs to see which employee was at the premises at that time and I saw multiple error messages that a deactivated account tried to connect to wifi.
That deactivated account belongs to an ex employee who (for some reason) made a deal with management that he could still have a key for a few months until he moved all his stuff out of the building (don't ask..).
What now
Legal has taken over, I did my part and the rest is over my pay grade.
For me it was a very interesting challenge and I'd like to thank every person on reddit who helped me with one piece of the puzzle.

Comment using SSH! Info
